Back in May of last year we noted that cyber security company Trend Micro was failing to keep the installation of WordPress on their blog up to date. What stuck out about this was that this shouldn’t have happened, as WordPress has an automatic background update feature that would normally have done the updates without requiring any interaction by someone at Trend Micro. So either there was some incompatibility between their hosting environment and that feature or they unwisely disabled the feature without making sure to promptly do the updates manually instead. If it was the former, then they could have probably helped not only themselves, but others by working with WordPress to fix the cause of those updates not occurring.
Fast forward to last week where it was reported that another one of their blogs was attacked due to a vulnerability in WordPress that would have not been possible to exploit on the website if they either had gotten automatic background updates working or if they had started promptly updating manually.
The response from the company’s “Global head of security research” makes it sound like the company has no idea what they are doing:
“We got reports from many researchers, regarding attacks using this vector and we deployed a custom policy to block the attacks,” he explained.
“Unfortunately there are many different URLs attackers can use to carry out the same attack, so a couple of fake ‘articles’ ended up posted on CounterMeasures. We have responded and shut down the vulnerability completely to resolve the issue
“Just serves to demonstrate something that I have often repeated in presentations, we are all a potential victim of digital attacks and we can’t afford to take our eyes off the ball at any time. The best way to respond to any attack of this nature is with honesty and alacrity, and that’s what we have endeavoured to do.
“Of course technology and best practice can mitigate the vast majority of intrusion attempts, but when one is successful, even one as low-level as this, you are more defined by how you respond than you are by the fact that it happened.”
The really simple solution to prevent this vulnerability from being exploited is to make sure you updated from WordPress 4.7.0 or 4.7.1 to 4.7.2, but there is no mention of that. Instead they make some mention of a “custom policy to block the attacks”, which is not necessary if you just updated to 4.7.2.
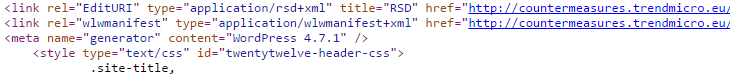
Amazingly as of this morning the blog is still running WordPress 4.7.1, as can easily be seen by viewing the source code any page on it:
The main Trend Micro blog doesn’t contain a meta generator tag, which makes it easy to spot what version is in use, but if you look at the CSS and JavaScript files being loaded on it you can see repeated use of “4.7.1” in the URLs, which tells you it is also on WordPress 4.7.1:
Defining Trend Micro by their response to getting attacked rather than their failure to take best practices doesn’t seem to make things better here, since they still have failed to properly respond to the situation by updating WordPress. Since they can’t handle the basics, you really would have to wonder about their handling of more serious things. Or you would if the wasn’t already evidence they can’t.