When it comes to the security of websites the situation isn’t good these days. Who’s to blame for that? Well there is plenty of blame to go around, but in dealing in the field we can say that one of the big culprits is security companies. The reality is that most of them don’t know and or care much about security, so they end up in many cases being counter productive to improving security. You won’t hear much about that, as these companies seem to have realized that as long as they all keep quiet about how bad they all are then they can get away with it. That has lead to what appears to be a de facto code of silence in the industry, which we have come to notice since we have pointed out problems with security companies’ products and services on a number of occasion and have had more than a few people contact us and tell us we shouldn’t being doing that. They have never were claiming that we had said something false, just that we shouldn’t be pointing out problems, which obviously sounds rather odd. In one recent case someone from a security company said that if we kept doing this, other security companies would turn “against you as it already happened to others in the past”.
Recently though a couple of web security companies with a focus on WordPress security criticized each other. Though one of them, Sucuri, ended up making a persuasive case that you should avoid them as well as the other company (which seems to be a good example why these companies normally keep quiet).
Last week Sucuri put out a post on their blog, Security Through Confusion – The FUD Factor. While the post doesn’t mention any companies by name, in a now deleted tweet they specifically mentioned the company Wordfence, who wrote a couple of posts that pointed to problems with Sucuri’s service (not surprisingly considering Wordfence’s poor understanding of security, they missed a key element of the topic). If you are in even vaguely familiar with the truth about Sucuri, you can’t help but notice how much of their post applies to them as well.
In several of the early paragraphs they describe companies as using FUD (fear, uncertainty, and doubt) to sell products:
FUD is very common in the infosec domain and used to gain advantage over competitors. It is often done by companies when they find themselves hurting financially, desperate for attention, lacking in adoption or the perceived real value of a product does not materialize. The goal is simple. Do whatever possible to divert attention and confuse an audience so that they buy X product.
and
In a crowded space like this, where anyone can be an expert, how are these organizations supposed to stand out? Unfortunately, the apparent answer to some seems to be to grow through the employment of disinformation strategies, the FUD factor.
More concerning is that some might not be doing it intentionally. They don’t understand security and are mixing FUD with misinformation and taking advantage of the average low-level aptitude of many WordPress users. That creates this concept of Security Through Confusion.
Next up the they have list of FUD triggers, which are “designed to help you know if you’re being deceived.” One of those is
An organization who claims “We’re the best!” or “We’re the experts!” or “We beat everyone by a wide margin!” –> Everyone is the best in their own eyes.
You don’t have to look far to see Sucuri doing that, here is the first sentence of the description page for their WordPress plugin:
Sucuri is a globally recognized authority in all matters related to website security, with specialization in WordPress Security.
Seriously, they wrote that. And now they are telling you to watch out for just that thing.
Right after that in the post they write this:
If you see any of these red flags it’s time to approach them carefully. In some instances, you’ll want to run the other direction quickly. Instead, spend the time to perform some critical thinking when working with an organization. Why are they making these claims, and is there anything that is supporting these claims?
Next they write this:
The more challenging triggers are those that are technical because not everyone is able to appreciate the nuances of an argument. You hear what you perceive to be an authority and believe them to be accurate.
This could apply to many things we have seen with Sucuri, but let’s look at one. Before that though, let’s look at example of this they provide.
Plugin creators that misuse terminology. An example of this would be claiming they are the only “defense in depth” solution as it contradicts the very idea of a defense in depth strategy.
It was just at the end of last month we looked at an example of them not having a clue what a brute force attack is, that is despite it being a common enough term that it has a Wikipedia page. That is only really the tip of the iceberg though. As we discussed back in August, either Sucuri doesn’t understand that brute force attacks against WordPress admin passwords are not happening or they are intentionally misleading the public to think they are. They even have a page that supposedly tracks brute force attacks against WordPress, but instead highlights that they are not happening.
One of the final elements of the post ends up pointing to them not being able to provide proper protection. They state:
A protection product should have enough threat-detection and analysis research to share.
We can say without any doubt that when it comes to security vulnerabilities in WordPress plugins, which is a major source of WordPress hackings, that Sucuri isn’t failing on the threat detection front based on the work we do for our Plugin Vulnerabilities service. One of the things we do to keep track of vulnerabilities in WordPress plugins is to monitor our websites and third-party websites for hacker activity. Through that we have found numerous vulnerabilities that exist in the then current versions of plugins, which hackers are have been probing for usage of, and would likely be targeted by hackers. When we started finding those we figured that other security companies would also be spotting those as well and wanted to see how our response time compared. You would assume that Sucuri would be looking for those as well, otherwise how are they supposed to protect against them if they are not aware of them. Much to our surprise we found that the other security companies are not spotting these. Through our work we have we have been able to insure many of those vulnerabilities get fixed, so even those not using our service are getting improved security thanks to us. By comparison, no one was given any additional protection by Sucuri, since they were not even aware of the vulnerabilities.
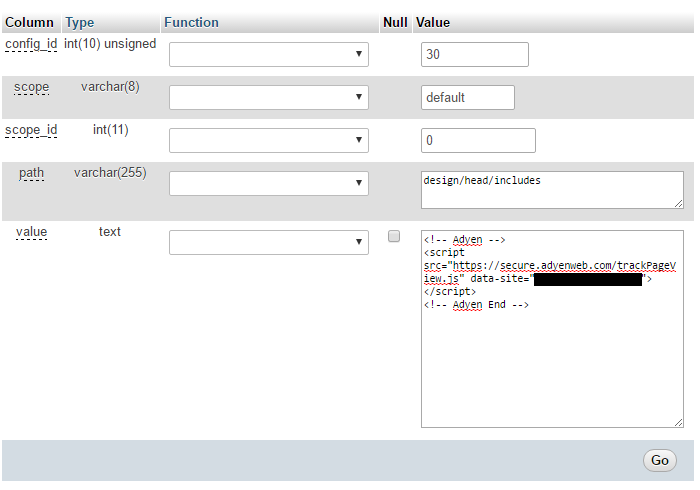
The one time that Sucuri mentioned one of those vulnerabilites it just went to show that they don’t really know what they are doing. The post starts with the following image:

While they proclaim this to be their “security disclosure”, we had actually disclosed the vulnerability a couple days before, which they were aware since they had repeatedly visited our post before releasing their post.
Here how the post originally started out (it was later edited after we had gotten news outlets to accurately reflect who had disclosed the vulnerability):
For the last few days, we have noticed an increasing number of websites infected without any outdated plugin or known vulnerability. In most cases it was a porn spam infection. Our research team started to dig into the issue and found that the common denominator across these WordPress sites was the plugin WP Mobile Detector that had a 0-day arbitrary file upload vulnerability disclosed on May 31st. The plugin has since been removed from the WordPress repository and no patches are available.
In that there are several huge red flags. Let’s start with the fact that Sucuri did not detect this vulnerability as it was originally being exploited, which they should have been able to do. We were able to do that and we don’t claim to be a “globally recognized authority in all matters related to website security”. Right there you can see they don’t have “enough threat-detection”. Then they fail on the “analysis research” front as well. When you are cleaning up a hacked website one of the basic steps is to determine how the website was hacked and you do that in large part by reviewing the log files. We know that Sucuri didn’t do that in this case, because if they did they would have easily found the vulnerability. Instead for some reason they were relying on trying to find a common denominator between the hacked websites (which shows they lack even basic skills). If we hadn’t already identified the vulnerability in the plugin they may have still been in the dark.
The fact that they didn’t looks at the logs in this case isn’t an aberration, if you take a look at a recent infographic they put together on cleaning up hacked WordPress websites, you will see there is no mentioning of determining how the website was hacked. That is despite that being one of three main components of hack cleanups. This point to the fact that they don’t properly clean up hacked websites and that they can’t properly protect websites as they don’t even know what the real threats out there are.
Also problematic on the “analysis research” front is that they didn’t mention that the vulnerability was only exploitable if you had PHP option enabled that is known to permit just this type of vulnerability. We prominently mentioned it in our post, so they were aware of it. Either they didn’t understand the significance of it or they didn’t want to mention it, since knowing that would allow a lot of people to easy see that they were not vulnerable and it would also show that you can actually take actions that will protect your website, instead or relying on a paid service.
Another one of the last things they say in the post is this
Be mindful of bold claims with no supporting data, or extremely vague descriptions.
If you look at how they promote their service, they also line up with this.
On their homepage here is how they advertise their protection as:
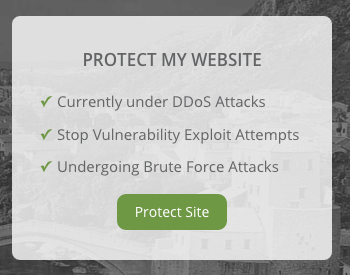
Beyond the fact that almost no one is actually undergoing brute force attacks ever (they really are pushing that falsehood), as we just discussed Sucuri isn’t even aware of many vulnerabilities, so their ability to protect against them is limited to say the least (also it can be incredibly easy to get around their protection, as well touch on in a future post).
If you click the link you will get a whole host of claimed protections, without any supporting data:
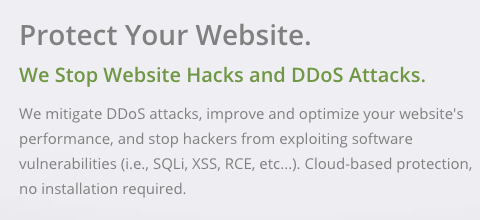
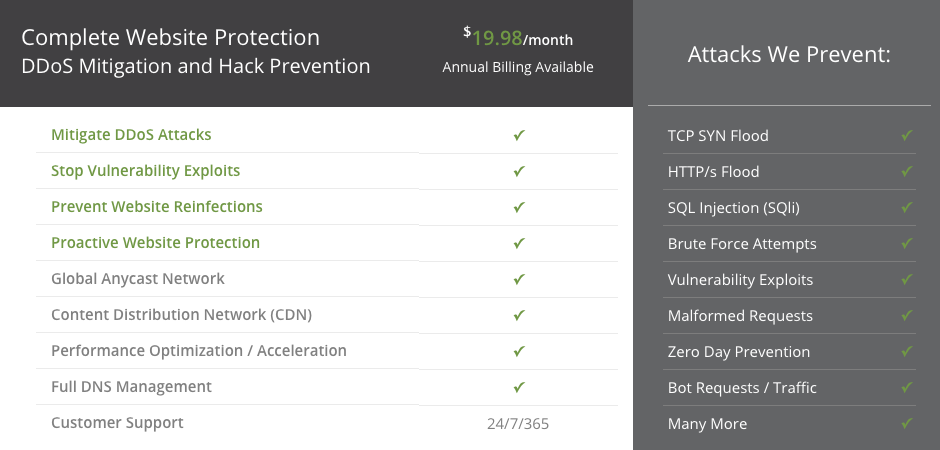
Their claim of “Zero Day Prevention” also should be a red flag. A zero-day vulnerability is any vulnerability that is being exploited before the developer of the relevant software is aware of it, so to prevent those you are really saying you can prevent any vulnerability from being exploited, which isn’t all that believable.
Help Improve Security By Warning Others About Sucuri
As long as bad security companies like Sucuri are to flourish, security companies are going to continue to be an impediment to improving to improving the security of websites. So by letting others know that they should avoid Sucuri, you will be helping to improve the situation. You don’t need to take our word that they should be avoided, Sucuri has made the case themselves that they should be avoided.