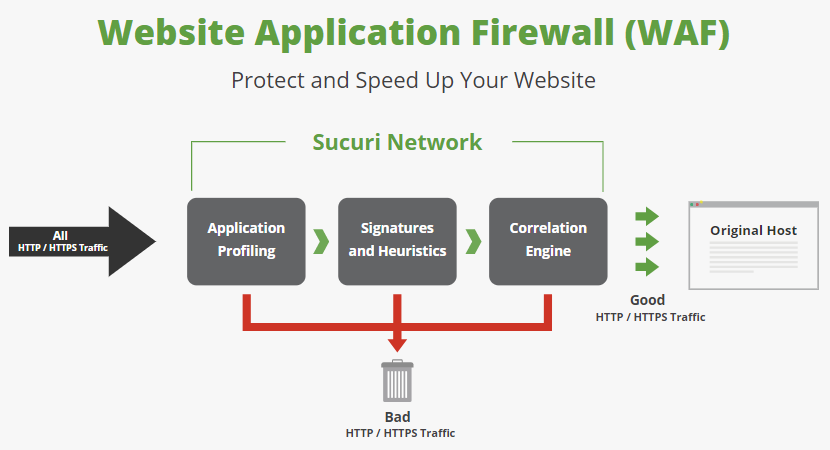
Earlier this week we looked at how the website security company SiteLock compared itself to competitors. What stood out in that is their idea of security isn’t focused on securing websites, but on instead leaving them vulnerable to being hacked and then trying to incompletely deal with the result of that. That is a good way for them to make money, but it is bad for everyone else. They are not alone in doing that though, as the comparison page for another company, Sucuri, shows.
The main portion of the page is a comparison chart, but before that is text that seems more important in terms of understanding what Sucuri is actually doing and not doing. It starts:
Our constant research keeps us ahead of competitors.
The unique insights shared by Sucuri Labs and the Sucuri Blog have earned us press and media mentions from top news outlets, industry blogs, and cybersecurity journalists.
The reality here is that their postings seems to be focused on getting press coverage instead of actually keeping ahead of competitors in terms of protecting websites. If you look at their blogs they are focused on the after effects of websites being hacked instead of on how they are getting hacked in the first place. That isn’t a good sign for their ability to protect websites, since what is important is how they got hacked, not what was done after that. Since not only do you need to know how they are hacked to effectively protect against those things, but if you are protecting them, the after effects of hack don’t matter since they won’t have happened.
When they have actually discussed how websites are hacked it actually shows they are way behind. In one recent instance of that they were notified of a vulnerability involving two WordPress plugins weeks after it had been discussed on the blog of our Plugin Vulnerabilities service and weeks after the free companion plugin for that service had started warning people about the vulnerable versions of the plugins. So Sucuri isn’t even able to stay ahead of people just following that service’s blog, much less competitors that actually do the research they claim to do.
Next up is this:
A safe internet is our mission, so we offer free tools.
We maintain a free website scanner and guides to help you fix or prevent website hacks. Sucuri is recommended by customers and web professionals in over 60 case studies.
As we have discussed in the past, their website scanner is to put it politely, incredibly crude. For example, as of year ago it was falsely claiming our website had been defaced on the basis of a page on it being named “Hacked Website Cleanup”. Where that gets much worse and seems to dispute their claim that the “a safe Internet is their mission”, is that instead of presenting the questionable results of that scanner in a neutral fashion they go in to full scare mode at detection of a possible issue. It seems their real mission is to take as much money from people without a concern if that involves falsely claiming that websites are hacked. Doing that goes against two of their four claimed values:
Helpful
When a website is hacked or under attack, a website owner is at their most vulnerable state. We will be the calm in the virtual storm, standing by to restore peace of mind.
Trust
The security space is filled with snake-oil and unnecessary FUD (fear, uncertainty, and doubt). We are committed to building services in the best interest of website owners.
In reality they are taking advantage of people when they are at their most vulnerable and spreading the FUD they claim they are against.
Looking at one of their guides it shows a good indication about their lack on focus on securing websites. In the guide for dealing with a hacked WordPress website, there are numerous ads for their service, but there is no mention of one of the three basic components of a proper hack cleanup. That being, trying to determine how the website was hacked. Websites don’t just get hacked, something has to go wrong, so if you don’t figure out what went wrong, you can’t be sure you have fixed that.
There seems to be a good reason for information on determining how websites are hacked being missing, from everything we have seen Sucuri usually doesn’t do that when cleaning up websites (and when we have seen them doing that, they didn’t seem to have a basic grasp of how it should be done). For a company that is supposed to be protecting websites from being hacked, that is fairly big issue since it would severely limit their ability to protect other websites from being hacked, which might explain how they market the service, which we will get to in a bit.
Getting to the main portion of the page, which is a chart that compares Sucuri to other services, just a quick glance shows that it contains false information. In the chart they claim they offer “Complete” hack and malware cleanups:
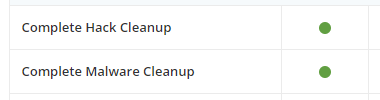
The reality is that they don’t do two of three basic components of a proper cleanup. Those being securing the website (which usually involves getting the software brought up to date) and the previously mentioned trying to determine how the website was hacked.
Right before the comparison chart is paragraph that begins:
We encourage you to research your options, read online reviews, chat with our team, and make an informed decision about who to trust with your website, reputation, and business.
What is completely missing from that page (or Sucuri’s website in general) is any evidence, much less from independent testing, that their service is actually effective at protecting websites. You can’t possibly make an informed decision on a security service when the most important piece of information is missing. There are two possible reasons why that is missing. The first being that they don’t actually have any idea is their service is effective, which based on everything else we have seen about them wouldn’t surprise us. The second is that they know it isn’t effective, but they realized they can get away with that.
(Reading online reviews is not a good way to make an informed decision since, for example, you can find reviews praising services despite the service failing to properly clean up hacks repeatedly.)
What makes that lack of evidence more striking is that on their homepage they provide several other measures of their service:

Touting how many websites they clean up seems like it could be a good indication that the service isn’t actually effective at protecting websites, since if they could do that that should be the thing they tout and they shouldn’t be doing many cleanups (other than for new customers).
The fact that on the homepage they twice tout that their services that are supposed to protect websites, includes “unlimited” cleanups also seem like a good indication of that:
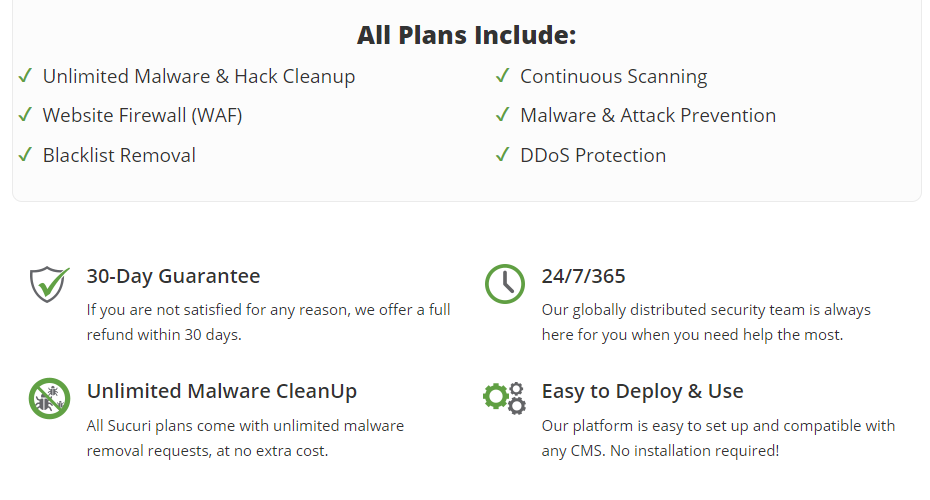
If websites were actually being protected they wouldn’t be hacked and therefore need to be cleaned up repeatedly.
Everything we have seen and heard, including people frequently contacting us looking for a security service that works after using one that didn’t, indicates that security service like Sucuri provides do not do a good job of protecting website. If you actually want to do something that will protect your websites, doing security basics will actually protect your website from most hacks.
If your website has been hacked you want to make sure to get it properly cleaned up, which involves removing anything the hacker added to the website, securing the website (which usually involves upgrading the software on it), and trying to determine how the website was hacked and fixing that. Many companies, including Sucuri, cut corners. So simply going with a well known company doesn’t mean that you are going to get a good result, in fact what we have seen is that the biggest names are usually very bad at security (lying about things has been effective method to make security companies popular, but it doesn’t help to make them good at security).