When it comes to the web security company SiteLock, one of the frequent complaints is that they and their web hosting partners falsely claim that websites have malware on them. After that happens the web hosting company frequently suspends access to the website and pushes the customer to hire SiteLock to clean up not existent malware. We thought it would be useful to look at an example of this we were recently consulted on, as those dealing with the possibility of a false claim should know a number of things when dealing with it.
This situation involved the web host Bluehost. Bluehost is one of many brands the company Endurance International Group (EIG) does business under. Some other major ones are A Small Orange, FatCow, HostGator, iPage, IPOWER, and JustHost. The company’s web hosting brands are very open about having a partnership with SiteLock, what they have, at least in the past, refused to acknowledge publicly is that partnership involves EIG getting 55 percent of revenue for SiteLock services sold through that partnership (that information was disclosed to investors). That obviously raises some serious questions and it probably explains in large part a lot of the problems that arise from that partnership. What they also don’t disclose to their customers is that the majority owners of SiteLock are also a member of the board and the CEO of EIG, so they are well aware of SiteLock’s practices.
What we have repeatedly said is that if you get contacted by SiteLock or one of their web hosting partners claiming that the website is infected or otherwise is hacked, is that should not ignore it. While there are plenty of situations like the one discussed here where there is a false claim, the claim is also often true. For a hacked website, the longer you wait to do properly clean it up, the bigger the problem can be. Instead we recommend that you first get any information that SiteLock and or the web host will provide and then get a second opinion as to whether the website is hacked. We are always happy to provide that and we would hope that other security companies would as well (when someone contacts us about a hacked website we always make sure it is actually hacked before taking on a cleanup).
One of the reasons for getting a second opinion is that someone familiar with hacked websites should understand how to easily check the validity of the claims made. While someone not familiar with the situation might try doing checks that won’t necessarily be very useful. In this situation one the things the website’s owner did was to download a copy of the website’s files and run them through a malware scanner. That likely is going to fail to identify many files that contain malicious code because a malware scanner for a computer isn’t designed to detect those files (our experience is that scanners designed to scan website files don’t produce great results either).
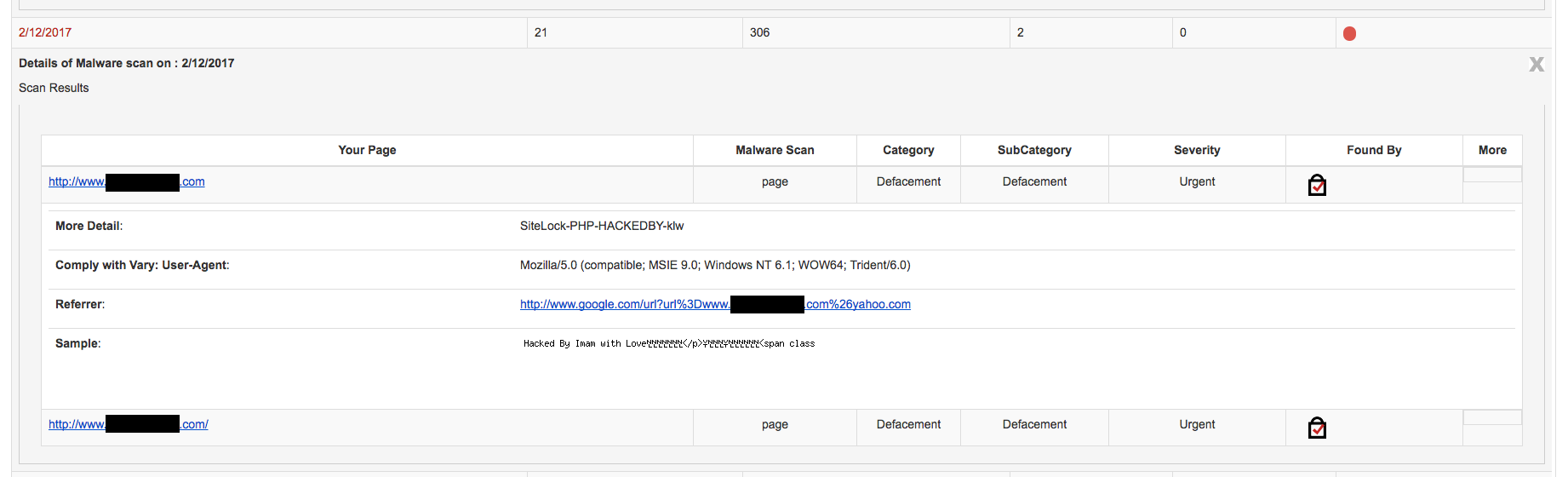
When we were provided the information that the website’s owner had received, the first element that caught our eye was this result of SiteLock’s malware scanner:
What was shown was rather odd as the malware scanner claimed to have detected a defacement hack (labeled as “SiteLock-PHP-HACKEDBY-klw”), which isn’t malware. So at best the scanner was incorrectly labeling a hacked website as containing malware, when it had a different issue.
More problematic is that it looks like they might are flagging websites as being defaced just because they have text that says “hacked by” something. That could produce some rather bad false positives, since this post itself could be claimed to contain malware simply by using that phrase. They also mark that detection as having a severity of “Urgent”, despite that.
So was the website defaced as that scan seemed to indicate? The website was taken down by the point we were contacted, which wouldn’t need to be done just because there was a defacement and makes it harder for someone else to check over things (whether intentional or not, it seems like something that makes it easier to push someone to hire SiteLock to resolve the issue). Looking at the Google cache of the website’s homepage though, we were able to see what happened.
The website’s page contains a section that shows RSS feeds items from other websites. One of those websites had been impacted by a vulnerability in outdated versions of WordPress that allowed defacing posts and the results of that defacement was showing on this website:

That “hacked by” text on showing there didn’t mean this website was infected with malware or otherwise hacked and the website didn’t pose any threat. That is something that anyone from Bluehost or SiteLock familiar with hacked websites should have spotted by looking over the website for a few seconds, but clearly that didn’t happen, even when they suspended access to the website. Both of them have an incentive to not check to make sure the website is hacked, since they have monetary interest in selling security services in this situation even though they are not needed. As we mentioned recently it appears that when you are in contact with SiteLock you are dealing with a commissioned sales person, not a technical person, so they might not even understand what is actually going on either (one situation we looked at recently would strongly seem to indicate that as a possibility).
Looking at the files that Bluehost had listed as being infected, they were just cached copies of the content from the website that had the RSS feed section in them. So there wasn’t any malware in them.
It also seems that no one from Bluehost or SiteLock bothered to contact the other website to let them know that there website was actually hacked, seeing as it was quickly fixed after we notified them of the issue they had.
At this point the website’s owner is planning to move to a new web host, which doesn’t seem like a bad idea (we think that people should avoid web hosts that have partnered with SiteLock even if they have yet to run into this type of situation).