When it comes to improving the security websites one of the major roadblocks we see is that often the security industry is pushing people in the wrong direction, a direction they themselves are heading. Instead of focusing on security basics they are pushing people to more advanced solutions, which are not necessarily better than doing the basics. As an example of that take Trend Micro that decided instead of keeping WordPress up to date with security updates (which normally are applied automatically) they would try to use some solution to block attacks, which didn’t stop one of their websites being successfully attacked. Even after that, they didn’t update WordPress, which would have prevented any chances of the attack being successful in the first place.
The other day we came across Cloudbric, which “is a cloud-based web security service” when they helped to spread false web security information put out by SiteLock and the repeated by SC Magazine. We were curious as to what kind of web security company would be unaware that they were spreading information that was rather obviously false and went to take a look into them we found that they were also running an outdated version of WordPress on their website, while misleading people about what protects websites.
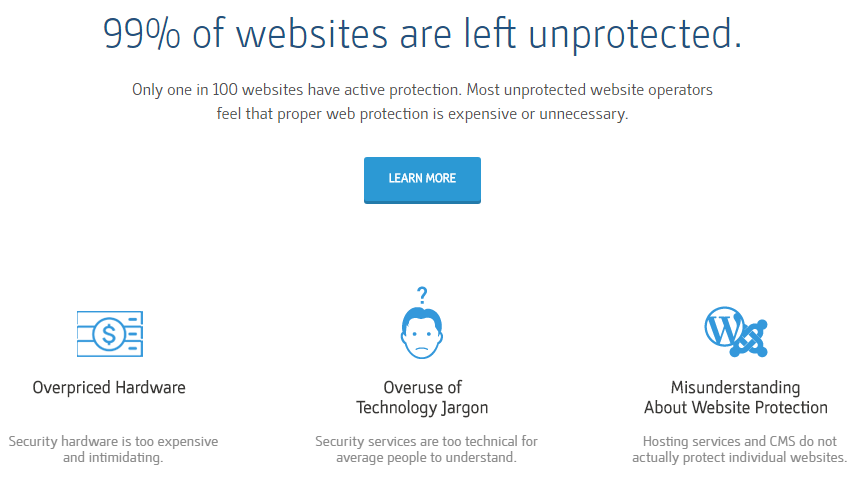
The company claims that 99 percent of websites are left unprotected, based on incorrect notion that active protection is the only protection:
As was the case with Trend Micro, active protection can actually fail to provide protection over passive protection. So the claim that “Hosting services and CMS do not actually protect individual websites.” isn’t true, as they do to varying levels.
Cloudbric seems to really believe the misleading information they are giving others as they are still running WordPress 4.2.2:
![]() That version was superseded with the security update 4.2.3 back in July 2015. Normally that and the subsequent 4.2.x updates would have been applied automatically due to WordPress’ automatic background updates feature, so either Cloudbric disabled those or their server environment has an incompatibility with that (which they could help WordPress to resolve). After 4.2.3, they have missed the next 10 security updates: 4.2.4, 4.2.5, 4.2.6, 4.2.7, 4.2.8, 4.2.9, 4.2.10, 4.2.11, 4.2.12, 4.2.13.
That version was superseded with the security update 4.2.3 back in July 2015. Normally that and the subsequent 4.2.x updates would have been applied automatically due to WordPress’ automatic background updates feature, so either Cloudbric disabled those or their server environment has an incompatibility with that (which they could help WordPress to resolve). After 4.2.3, they have missed the next 10 security updates: 4.2.4, 4.2.5, 4.2.6, 4.2.7, 4.2.8, 4.2.9, 4.2.10, 4.2.11, 4.2.12, 4.2.13.
You have to wonder if when Cloudbric says that “Most unprotected website operators feel that proper web protection is expensive or unnecessary.” that is based on their own feelings.
More Tolly Group Testing
One of the things we take a look at with companies providing security services that claim to provide protection is if they are providing real evidence to back up their claims (so far we haven’t seen one that provides that). With Cloudbric they claim their WAF provides “the most effective security”:
Penta Security’s web application firewall provides the most effective security. It was rated considerably higher than the widely known vendor Imperva’s technology. Cloudbric is known for higher performance and greater functionality than Incapsula. Sitelock and Sucuri are built on an open-source engine called Mod Security.
(They also claim to that SiteLock’s WAF is based on Mod Security, when in fact they actually reselling Incapsula’s service, so that make us suspicious as their claim about their service.)
That claim seems to rest on a report by the Tolly Group. If you follow our blog you might recall the test that they did for SiteLock, which would it would probably be accurate to describe as rigged, as SiteLock provided the samples that their product were supposed to be detecting in the test.
Looking in to the report for this company the same thing was true:
A collection of 1,000 attacks were used to test the effectiveness of each solution, in both default and maximum security settings. This was run multiple times to ensure accuracy. The attack set was a random subset of attacks collected by Penta from Exploit-DB, 1337 Inj3ct0r, SQL Injection Wiki, fuzzdb and other online security communities.