One of the problems when it comes to improving security is there is so little accurate information out there. Often times security companies are putting out misleading or outright false claims. When their information is repeated by security journalists the quality of it usually degrades from the already often low quality. As example of what happens when security journalists repeat security companies’ claims was something we recently ran across related to SiteLock.
In an article on CISO MAG the following claim was made that seem unlikely to be true:
SiteLock’s analysis also showed that a website’s content management system had an impact on overall security. Forty-four percent of websites using WordPress CMS had not been updated for over a year at the time of filing this report.
We went to look into that because that because it seemed like it would be a good example of SiteLock getting stuff wrong, but in looking at the report what SiteLock actually claim was very different. What they said hasn’t been updated in a year are plugins in the Plugin Directory:
44% of plugins in the WordPress repository have not been updated in over a year
It is important to note that doesn’t mean that those plugins are somehow insecure, though if plugins are not at least being updated to list them being compatible with newer versions of WordPress there is a greater chance that if there is a security vulnerability found that it will not be fixed promptly or at all (though in reporting many vulnerabilities to WordPress plugin developers through our Plugin Vulnerabilities service even very recently updated plugins are not always fixed in a timely manner or at all).
Making that incorrect claim seem odder is the beginning of the next paragraph of the CISO MAG article:
Nearly seven in 10 infected WordPress websites had the latest security patches installed, but were compromised because of vulnerable plugins.
If “nearly 7 in 10 had the latest security patches” then it wouldn’t make much sense that 44 percent of them hadn’t been updated in the last year.
The claim that the website “compromised because of vulnerable plugins” is also not what the report says. Instead it says:
69% of infected WordPress websites were running the latest security patches for WordPress core at the time of compromise.
This data illustrates that even when running a version of WordPress with all of the latest security patches, a vulnerable plugin or theme can just as easily lead to a compromise.
Looking at the rest of the report there were a couple of other WordPress related items that stood out. The first thing is a mention of “publications” that “inaccurately implied that WordPress websites which aren’t running the newest version of WordPress are insecure”:
NOTE: Many publications have inaccurately implied that WordPress websites which aren’t running the newest version of WordPress are insecure. As of the end of Q2 2017, the WordPress community actively provided security fixes for all versions of WordPress from v3.7 to the current v4.8. Our research takes into account each security patch release for every version of WordPress in Q2 2017. For example, WordPress v3.7.21 contains all of the same security fixes implemented in the current version, v4.8. In theory, this makes v3.7.21 as safe as v4.8.
We are not sure what publications they are referring to, but one security company comes to mind, SiteLock, which has been falsely claiming that websites are insecure when running the latest version of older versions of WordPress. We first noticed this back in September of last year and SiteLock was clearly aware of that post, but as of at least June they were still doing this.
Another element of the report repeats a WordPress related falsehood from SiteLock that we debunked in April:
Fake Plugins: Trend Maricopa
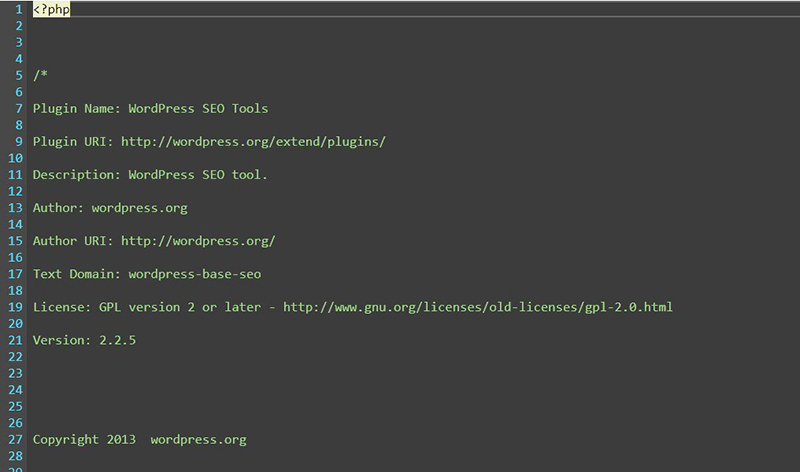
In what SiteLock Research would call an “oldie but a baddie,” we saw a trend in the first week of April that centered on the return of an old trick targeting WordPress websites where malware disguised itself as a legitimate forum plugin in the WordPress plugin directory. This ruse, while easily dispatched by specialized malware detection systems, would just as easily escape the concern of an untrained eye. Fake plugin malware iterations continue to be developed and deployed because, quite simply, most people don’t notice them. In a world where the majority of website owners don’t take a proactive approach to malware prevention or remediation, persistent infections continue to be common.
The reality is the supposed legitimate plugin, WordPress SEO Tools, has never existed, whether in the Plugin Directory or otherwise. We don’t understand why SiteLock is continuing to peddle that falsehood when it is so easy to confirm it to be false.