Yesterday we discussed a situation where the WPScan project didn’t bother to notify the developer of a WordPress plugin or the wordpress.org Plugin Directory about a vulnerability that they knew about. Some might excuse WPScan’s responsibility to alert them based on the fact that the vulnerability was discovered by someone else and already publicly disclosed. After running in to that situation we took a closer look at the WPScan project and found something more troubling. Back in March they started discussing a backup plugin that wasn’t properly securing backup files made by it. The issue was quite serious since some of the backup files, which can contain sensitive information, made by the plugin could be easily found with just a simple Google search. In the thread no one even brings up the idea of notifying the developer of the plugin or the Plugin Directory about the issue, which would be the way to get it fixed. Instead there is some discussion in thread on how to further exploit the poor security of the plugin in the WPScan vulnerability scanner.
We are quite sure that no one ever bothered to contact the Plugin Directory about the issue because within hours of us notifying them last week the plugin was pulled from the directory pending the security being improved. Within a few days of that, security improvements were introduced to the plugin. Based on the plugin developer’s comment at the end of the thread it doesn’t sound like WPScan had informed them either.
What makes this particular troubling is that at the same time they are at least knowingly leaving websites insecure they are selling WordPress security services.
They are not the only ones selling security services involved in this. Prominently displayed on the WPScan homepage is a banner letting you know the project is sponsored by Sucuri:

We would ask why a security company would sponsor a project that seems more interested in exploiting security issues than fixing them, but we already know that Sucuri doesn’t have much interested in websites actually being secure. We have often been hired to re-clean websites that had previously cleaned by Sucuri. What we have found in those cases is that Sucuri didn’t do basic parts of a proper cleanup, including making sure the software on the website was up to date and determining how the website was hacked, which if done would have made it less likely that the website would be hacked again.
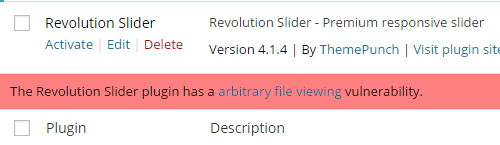

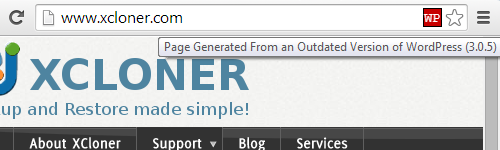
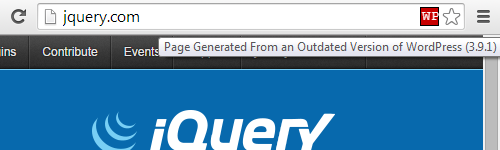
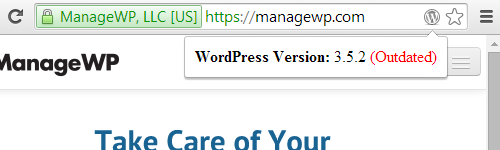
 Today we released a new version of the plugin that lists installed plugins that have not been updated in over two years. If you want to check if you are using any plugins that have not been updated in over two years install our
Today we released a new version of the plugin that lists installed plugins that have not been updated in over two years. If you want to check if you are using any plugins that have not been updated in over two years install our 