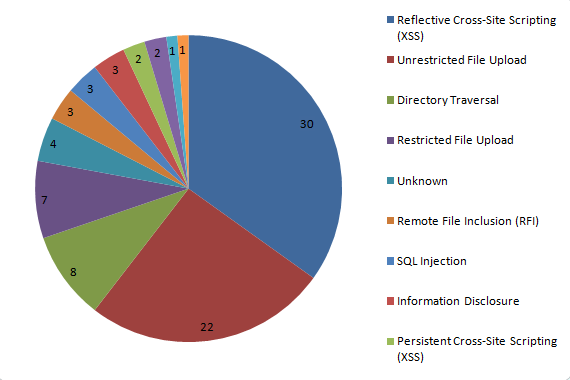
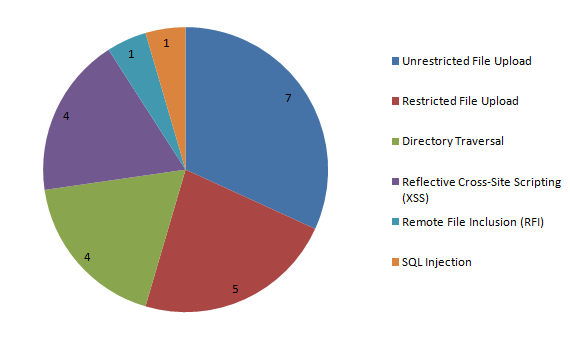
Ars Technica has been running a series of articles about the recent hack of several US Federal Trade Commission websites hosted at Media Temple. The latest reporting indicates that “critical vulnerability in some versions of Parallels’ Plesk Panel control panel software appears to have been key to the recent penetration”. A patch for the vulnerability was released in September, though the article mentions that Parallels didn’t send email alerting customers to the critical nature of the vulnerability until February. Media Temple’s failure to keep Plesk up to date goes back years and we unsuccessfully tried to get them to address the issue back in July of 2010.
Media Temple and Parallels are both part of the Hosting Security Forum, which is supposed to “share critical security information in order to protect the integrity of a customer’s data, their web presence, and online availability”. That organization’s website is running an outdated version of WordPress, 3.2.1, which might be a good indication as to the group’s level of dedication to security. Media Temple, as well as Dreamhost and other members of that organization, is also running outdated software on their website.
Warning Media Temple
Back in July 2010, during a period of hacks that were targeting Media Temple customers (but that Media Temple claimed was not due to their security failings), Media Temple made some long needed security improvements and asked for people to contact them if they were missing any security measures.
While cleaning up a hacked website running on their Dedicated-Virtual service we noticed that Media Temple was using a nearly two year old version of Plesk, which also meant that the other software that comes with Plesk was also two years old. We contacted Media Temple alert them to the need to keep that and other software running on their systems up to date and at the time we hoped that they would quickly resolve the issue as they were publicly claiming to want to improve their security.
Media Temple’s response was that there hadn’t been a known vulnerability in Plesk since 2007 and therefore they were secure. We don’t why they felt they didn’t need to keep their up to date just because there had not been known vulnerabilities, but in any case it wasn’t the whole truth. While the version of Plesk didn’t have any known vulnerabilities other software that came with that version of Plesk did have known vulnerabilities. We specifically brought to their attention there were apparently security issues in at least the versions of ProFTPd, Ruby, and phpMyAdmin that came with it. We never received any response after we brought that up. Overall, their response seemed to be more focused on creating the impression that they cared about security then about actually making sure they and their customers were secure.
During the email exchange they claimed they had recently put in place a policy that “requires us to patch any software with security flaws within 30 days of a patch being made available. For the most critical issues, such as a kernel exploit, we will patch immediately. ” We certainly would describe the vulnerability in Plesk as being a critical issue, but for some reason they didn’t feel the need to apply the patch immediately or even in the 30 day window.
Blame the Customer
When the issue of the hack was first surfacing Media Temple was quick to blame their customer for the hack and criticize them for running outdated software. While it’s true that many hacks are due to issues which the customer is responsible for and many of those are due to outdated software, it is irresponsible to claim that it was the customer’s fault without actual evidence to support that, especially to do that publicly. For Media Temple’s to do this is worse as during our email exchange they excused not keeping Plesk up to date on there not being known vulnerabilities, so they certainly should understand that just running outdated software doesn’t mean that it is vulnerable. To be criticizing a customer for running outdated when they don’t keep the software they are responsible for up to date makes the response appalling.
Unfortunately, Media Temple’s response to this incident isn’t out of line with the usual response that customer’ with hacking issues receive when contacting their web host about a hacking issue.
Media Temple Runs Outdated Web Software
Based on the rest of Media Temple’s actions it isn’t surprising that they fail to keep software running on their website up to date (while criticizing others for doing the same).
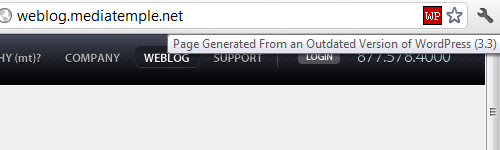 Their blog is running WordPress 3.3. The latest version, 3.3.1, was release nearly two months ago and included a “fix for a cross-site scripting vulnerability that affected version 3.3“.
Their blog is running WordPress 3.3. The latest version, 3.3.1, was release nearly two months ago and included a “fix for a cross-site scripting vulnerability that affected version 3.3“.
 The Media Temple Community Wiki is running a version of MediaWiki, 1.16.x, that hasn’t been supported for nearly three months. They also failed to apply the last three updates, all of which included security fixes, for 1.16.x. The oldest update they failed to apply, 1.16.3, was release over ten months ago.
The Media Temple Community Wiki is running a version of MediaWiki, 1.16.x, that hasn’t been supported for nearly three months. They also failed to apply the last three updates, all of which included security fixes, for 1.16.x. The oldest update they failed to apply, 1.16.3, was release over ten months ago.
You can get alerts for outdated web software, like the one the ones in the screenshots above, with Meta Generator Version Check extension (available for Firefox and Chrome).