We are frequently hired to clean up websites that another company was previously hired to clean up but then has been hacked again (or wasn’t actually cleaned up in the first place). In some cases we wouldn’t lay the blame on the company, sometimes hacks are well hidden and getting them cleaned up can take more than one cleanup (which you shouldn’t be charge extra for) and in other cases there are security issues that the company doing the cleanup can’t handle. For example, if your web host has a security issues then they are going to only ones who can fix that. What we find in most instances though is that company doing the hack cleanup has not done the basic elements of the hack cleanup.
When someone contact us about cleaning up a website that was previously cleaned the first question we asked is if the first company determined how the website was hacked. Determining how the website was hacked is important part of the cleanup as if you don’t know how it was hacked you won’t know if the security issue that allowed the website has been fixed. Considering that the websites have been hacked again it isn’t surprising that the answer we hear over and over is that they didn’t. But isn’t just that they didn’t determine how the website got hacked, the companies didn’t even try to determine how the website was hacked. Either these companies are knowingly cutting corners or they don’t care enough about the service they providing to know what work they should be doing. In either case what they are doing is highly unethical.
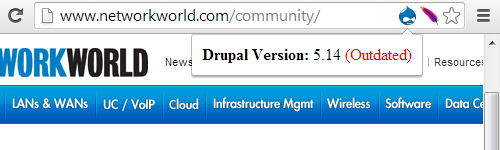
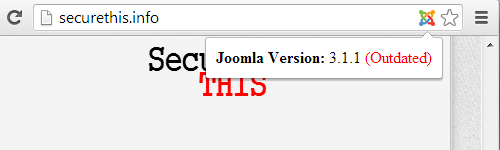
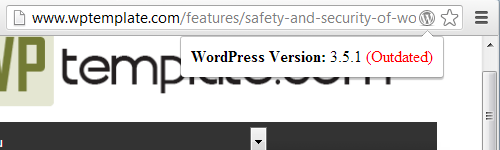
We don’t ask our clients who they previously hired, but they do bring it up from time to time. During recent cleanup of a Joomla website the previous company was mentioned and when we went to their website we noticed that they were running an outdated version of Joomla. Keeping the software running on a website is a basic security measure, so any company that doesn’t bother to do that really shouldn’t have anything to do with the security of other people’s website. We took a look around at companies advertising to clean up Joomla websites and we found that all of the companies were running out of date software. As warning to the public and as a reminder of how bad the current state of companies providing security services is we have highlighted them below:
Dean Marshall Consultancy (http://www.deanmarshall.co.uk/)
 Support for Joomla 1.5 ended in September 2012, so a websites shouldn’t be running it anymore (though many, including joomla.org, are still using it as we mentioned yesterday). As part of cleaning up a hacked website still running Joomla 1.5 you will eventually want to migrate it to a newer version, which doesn’t seem like a task for a company that still hasn’t done it for their own website.
Support for Joomla 1.5 ended in September 2012, so a websites shouldn’t be running it anymore (though many, including joomla.org, are still using it as we mentioned yesterday). As part of cleaning up a hacked website still running Joomla 1.5 you will eventually want to migrate it to a newer version, which doesn’t seem like a task for a company that still hasn’t done it for their own website.
Joomla Help Live (http://joomla.cmshelplive.com/)
 Joomla 1.7 is over two years out of date and more importantly it has a serious security vulnerability that we have seen being exploited.
Joomla 1.7 is over two years out of date and more importantly it has a serious security vulnerability that we have seen being exploited.
PennZac (http://www.pennzac.com/)
 Joomla 3.0.3 is ten months out of date and there have been four subsequent versions with security updates.
Joomla 3.0.3 is ten months out of date and there have been four subsequent versions with security updates.
US Joomla Force (http://www.usjoomlaforce.com/)
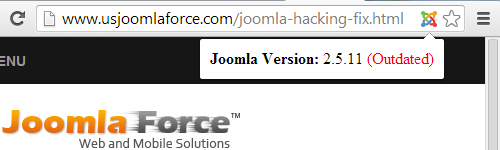 Joomla 2.5.11 is seven months out of date and there have been two subsequent versions with security updates.
Joomla 2.5.11 is seven months out of date and there have been two subsequent versions with security updates.
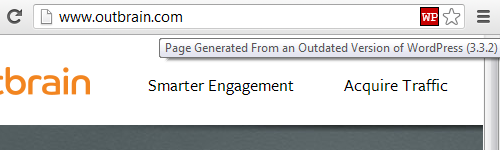
itoctopus (http://www.itoctopus.com/)
 WordPress 2.8.5 is over four years out of date and there have been 17 subsequent versions with security updates.
WordPress 2.8.5 is over four years out of date and there have been 17 subsequent versions with security updates.