Oftentimes when a website is hacked the web host will blame the hack on outdated software running on the website. From our experience they often do this without any evidence to back that up and in some cases they obviously haven’t even checked if the website is running outdated software since the website in question was using up to date software at the time of the hack. Based on that you would think that web hosts would be very careful when distributing software to their clients that they make sure that it is up to date, but as we keep seeing that isn’t the case. The latest example this came up while we were looking into GoDaddy’s bad response to the Drupal 7 vulnerability. We noticed in their Hosting Connection, which they say has been used to install 6.9 million apps, that they were still installing Drupal 7.32:
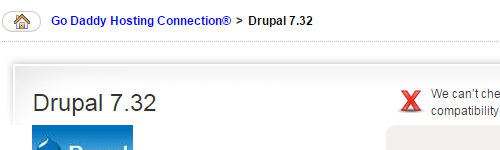
Drupal 7.33 was released last Friday and includes “numerous bug fixes”. Since the new version didn’t include any security fixes it wasn’t a huge issue that they hadn’t updated the version they installed yet. But then we started looking at the version of other software they were offering and things got much worse.
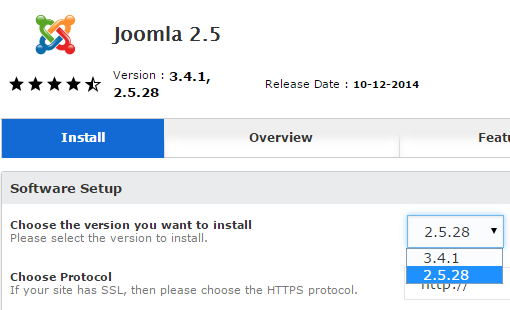
They are still installing Joomla 2.5.14:
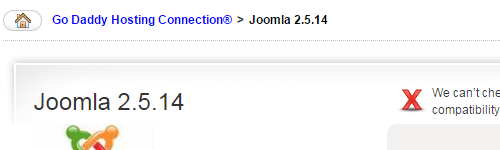
That version is now a year out of date, the next version was released on November 6, 2013, and GoDaddy hasn’t updated their Joomla version despite there having been four subsequent releases with security fixes (2.5.1.5, 2.5.19, 2.5.25, and 2.5.26).
Joomla is among the software GoDaddy lists as being the five most popular in the Hosting Connection and unfortunately isn’t the only one where they have failed to keep up with security updates. They are currently installing Simple Machines Forum version 2.0.6:
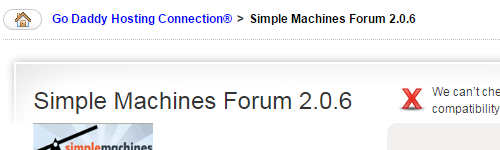
Version 2.0.9, which was released over a month ago, addressed “several security issues” and the developers recommended “that you update your forums immediately to ensure that your community is safe”.
Looking at other software we work with frequently we found more problems. GoDaddy is still offering MediaWiki 1.21.1:
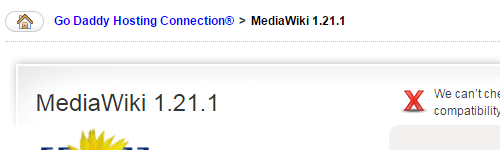
Support for the MediaWiki 1.21.x series ended back in June, so GoDaddy should have switch to a newer series by that point. Before that though they failed to update for any of the nine security updates (1.21.2, 1.21.3, 1.21.4, 1.21.5, 1.21.6, 1.21.8, 1.21.9, 1.21.10, and 1.2.11) released for the 1.21.x series.
Next up, GoDaddy is still offering OpenX despite it being re-branded as Revive Adserver over a year ago:
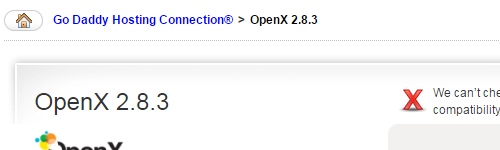
The version they are offering is nearly five years out of date, the next version was released in January of 2010, and they fail to update for the last eight security updates (2.8.6, 2.8.7, 2.8.8, 2.8.9, 2.8.10, 3.0.0, 3.0.2, and 3.0.5).
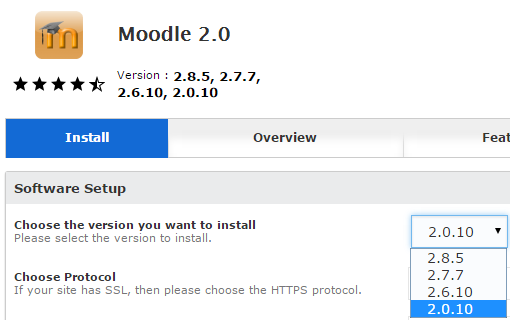
For Moodle they are still providing Moodle 1.9.19:
That was the last release of the Moodle 1.9.x series, for which support for security fixes ended entirely last December. Anyone unlucky enough to install this version and start using it now would discover they will have a lot of work to get it to a supported version as the upgrade from Moodle 1.9.x to 2.x is a major one and they will have to do at least two upgrades as you have to an intermediate upgrade 2.2.x before getting to a supported version.
GoDaddy’s Partnership with SiteLock
It gets worse from there, while GoDaddy is putting their client’s websites at risk they then want to sell them additional service to “Defend your website against hackers.”, which is done in partnership with SiteLock. We would ask how it is that SiteLock hasn’t informed them about the issue with outdated software but our past experience is the SiteLock doesn’t do the basic security check of making sure the software on a website is up to date, which would expect from a company that GoDaddy says provides the “most advanced and complete security solution available”, or make sure that software gets updated when they clean up a hacked website.