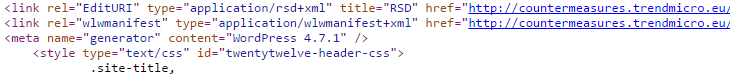
Last week we discussed that the website of Rudy Giuliani’s security company was running an outdated and insecure version of Joomla. Since then the website has been taken down. What we also mentioned in that post was that it wasn’t clear what his company actually did in terms of cybersecurity. Motherboard seems to have answered that question:
Since 2003, his consulting firm Giuliani Partners and its subsidiary Giuliani Security and Safety has at least nominally advised clients on cybersecurity, but people who have worked with his firm say the advice is focused more on liability mitigation for companies rather than implementing best security practices.
“If you hired them on a cyber engagement, they are going to tell you what your legal obligations are and how to manage the legal risk related to cyber,” a cybersecurity executive in New York who has experience with Giuliani Security and Safety and requested to remain anonymous told Motherboard. “Basically, not to prevent a Target [breach], but how to prevent a Target CEO being fired.”
Considering that from everything we have seen most security companies don’t seem to know and or care much about security, this isn’t as troubling to us as it should be for others not aware of what is going on in the industry.
In an interview Mr. Giuliani did with MarketWatch from a year ago, you get more of a sense of what the industry is all about:
MW: So Giuliani Partners began penetration-testing companies — attacking from the outside to find vulnerabilities hackers may exploit — back in 2003?
RG: 2004, 2005 by the time we got started.
MW: How many clients did you have back then?
RG: Maybe 30.
MW: Did you find that anyone cared about cybersecurity back then?
RG: These were all friends of mine, friends of his. They’d give me a nice meeting and they’d look at me, and they’d look at the bill. And the bill was high, but it wasn’t high for them — $10 million, $20 million, something like that. It wasn’t like the kind of money they’re spending now. (laughs)
From what we have seen of penetration testing we have a hard time believing the underlying cost of the work was a fraction of what was spent. A lot of it involves running automated tools over systems, which largely warn you about vulnerabilities that exist in outdated software (for which the money would be better served keeping the software up to date).
The next line in the article indicates that big dollars spent doesn’t necessarily produce results:
(Note: J.P. Morgan Chase had a $250 million cybersecurity budget when it was breached in 2014; CEO Jamie Dimon said after the breach that the bank would double cybersecurity spending.)
Newt Gingrich’s Outdated Website
Considering the prominence that cybersecurity has taken in US politics you might think that would lead to prominent players taking actions to make sure they are secured (by hiring someone, not doing themselves, obviously). That isn’t the case with the website of former House Speaker and Donald Trump advisor Newt Gingrich, gingrichproductions.com. The website is still running WordPress 3.7:
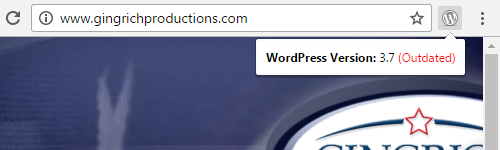
The next version of WordPress, 3.7.1, was released in October of 2013.
Keeping the software running a website update is a basic security measure.
What makes this a bid odd is that WordPress introduced a new update system in WordPress 3.7, which automatically applies minor WordPress updates. Along side that WordPress started releasing security updates for older versions of WordPress, so normally the website would have been getting security updates without requiring any manual intervention since then (the latest version of WordPress is still the only one official supported, so websites should still be keeping WordPress up to date with the latest major release). Seeing as the updates didn’t happen, either that feature was disabled or it had some conflict with the website’s hosting environment.
Whatever the cause, 14 security updates for WordPress 3.7 have been missed: 3.7.2, 3.7.4, 3.7.5, 3.7.6, 3.7.8, 3.7.9, 3.7.10, 3.7.11, 3.7.12, 3.7.13, 3.7.14, 3.7.15, 3.7.16, 3.7.17
Unlike the website of Rudy Giuliani’s security company, which looks like it might not have been actively managed since 2014. This website is still very much active, seeing as the News section of Gingrich Productions has entries from just days ago.