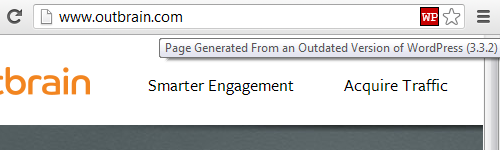
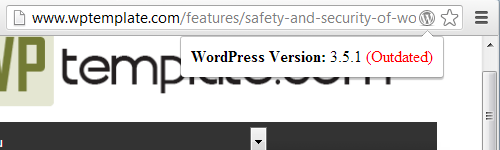
We have found that web hosts often prominently advertise their focus on security while not actually caring about security enough to even taking basic security measures. Lets take a quick look at Rackspace to see that in action. Rackspace has a whole section of their website dedicated to security. If you look over that you would probably be impressed. Though if look closely you might see warning signs. For example, they have a PDF about their “holistic approach to security” that was written by their Director of Product Marketing. Why is a product marketing person writing a security guide?
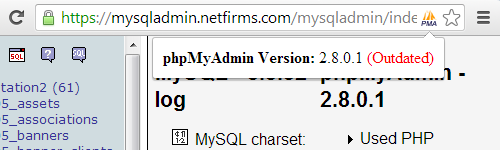
You don’t have to look hard to see that Rackspace don’t actually have much concern for security. A really basic security measure is keeping software running up to date. That way the software isn’t vulnerable to known security vulnerabilities that have been fixed in the software. An important component of many hosting services is phpMyAdmin, which allows administration of MySQL databases. If someone can exploit phpMyAdmin they can gain access to the database underlying a website. With that they could collect customer information stored in the database, they could create a new administrator account for a website to gain further access, or do other harmful things. If you believed Rackspace’s claims about their focus on security you would certainly expect they would be keeping their installation of phpMyAdmin up to date. Unfortunately for their customers they don’t:
The version they are running is over a year and half out of date (as the next version of phpMyAdmin was released in February of 2012). It gets even worse, Rackspace only upgraded to that version after a customer alerted them that they were running an outdated and insecure version of phpMyAdmin and took them six months after being alerted to that to do that upgrade.
According to the information on phpMyAdmin’s security page the version Rackspace is running contains a number of security vulnerabilities. The version they are using is so out of date that phpMyAdmin no longer lists if vulnerabilities impact that version, so it isn’t clear exactly how many there are.


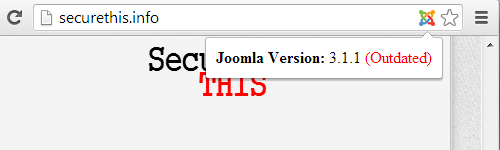
 The version they are using is not just a little out date. Support for Apache HTTP Server 1.3
The version they are using is not just a little out date. Support for Apache HTTP Server 1.3