When it comes to the security of websites one of the major problems we see is that often the basics are not being done (even by security companies), one of the most important is keeping software up to date, which prevents known vulnerabilities that have been fixed in a newer version of the software from being exploited.
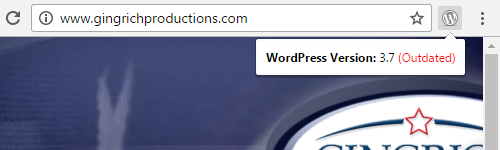
Back in 2013 the developers of WordPress took a step to protect websites running WordPress from this by introducing a new updates system in WordPress 3.7 that automatically applies minor WordPress updates (the ability to have major WordPress, plugin, and theme updates also exist in that functionality). Alongside that they started releasing security updates for older major releases that have that update functionality, in the form of minor updates. So unless something causes that feature to not work or it has been intentionally disabled, any websites still running WordPress 3.7 or above would still be being protected against vulnerabilities discovered in WordPress.
As far as we are aware only the most recent major version of WordPress is officially supported, so you should be making sure you are on the latest version, but those running older major versions should still be relatively secure as long as they are on the latest minor release of that.
Disabling those automatic updates cannot be done in the settings of WordPress, so it isn’t something that could be accidentally done. Instead someone has to make an active decision to do that (by using a plugin or making a change to a file) and it would generally be a bad one. The reasons for doing that usually seem rather bad, take for example the website of WordPress security plugin where that looked to have happened, the company behind later told us that had been done because they had modified core files, which you shouldn’t be doing (that the developer of security plugin would be modifying core files like that would be concerning on its own and it probably isn’t surprising then that we later found a couple of vulnerabilities in the plugin).
That brings us to fairly widespread reports of websites that have been hacked due to not having applied the latest WordPress update (without having looked at the websites’ data and logging we can’t say how many of those claims are true and how many of those websites were hacked due to other issues). One message that showed up about this in the monitoring of the WordPress support forum we do, to keep track of vulnerabilities in plugins for our Plugin Vulnerabilities service, had a troubling explanation for not being on the latest version:
WordPress 4.7.2 was patched at some rest-api vulnerability and some other stuff according to change log. I usually checkout the change log every time whenever an update is available. This was the first time I didn’t check that and only imagined the 0.1 version difference to be a slight upgrade. But I was wrong.
While some minor updates just include bug fixes (the last one being in April of last year), most are security updates. By comparison, a major update is not likely to introduce a security fix. So the updates you want to apply right away are the minor ones or better yet don’t disabled the automatic updates, so you don’t have to worry about making this decisions. Major updates, not minor updates are the ones that have more of a chance of causing a problem (say if a plugin hasn’t been updated to be compatible with the new version).
If you are still using a very old version of WordPress on your website, you may want to have a test of the upgrade done before upgrading the production website to the latest major version so that any issues can be resolved first. Doing a test of the upgrade is included in our upgrade service for WordPress.