When it comes to the poor state of website security one of the issues we see is that while too often people are not doing the basics of security, security companies are pushing all sorts of advanced security products that provide little to no value beyond what could be had by doing the basics. Sometimes those things are fairly connected, take for instance the cyber security company Lunarline that claims to have “clients in the intelligence community, DoD and nearly every cabinet agency”. In post on their blog back in July, No Website Is Immune From Cyber Attacks, they stated:
Reducing your risk of critical website attacks requires a multifaceted approach, but you can take the necessary steps regardless of your organization’s size. While you may be running vulnerability scans on your web servers, these scans can only find known issues, and weak points specific to your organization’s systems may go unnoticed. This is where skilled penetration testers come into the picture, using up-to-date real-world hacking methods to see where you could run into problems.
The reality that we see in dealing with hacked websites is the problems would have been prevented with pedestrian measures, say keeping the software up to date. That is something that Lunarline isn’t doing on that same blog:

It isn’t just that they have kept WordPress up to date, but they are not running the latest version of the outdated version of WordPress, 4.2, they are using, which is 4.2.10 (4.2.2 was released in May of 2015). All the 4.2 releases since then have include security updates.
For those not familiar with WordPress, that indicates something is wrong. Normally WordPress would have automatically applied the 4.2 updates due to WordPress’ automatic background updates, which were introduced in WordPress 3.7. There are two likely possibilities why those updates haven’t happened, the first being that they disabled the automatic updates and then didn’t handle the updates manual or there there is a problem with those updates occurring in their hosting environment and they also never bothered to manual update either. If it was the latter then helping WordPress to resolve that issue would help them, since they can’t seem to manage to the update themselves, and it would help anyone else with the same issue.
This isn’t the first time we have run into a situation like this. We previously discussed the fact that the maker of a WordPress security plugin’s website had an out of date WordPress installation. In that case they later contacted us and let us know that they had disabled the updates since they had modified core WordPress files, which you shouldn’t do. The fact that someone making a WordPress plugin couldn’t properly handle using WordPress built-in capability to modify it instead of modifying core files, makes what we found the next time we ran into them none to surprising. We found that their plugin was using custom for a security check instead of using WordPress built-in function for doing the same and that the custom code had a security vulnerability in it.
The outdated WordPress install on Lunarline’s blog isn’t the only obvious security issue with their website. They are also running an outdated version of WordPress on their School of Cyber Security website as well: 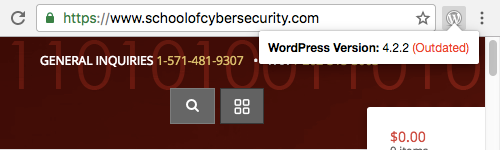
Their main website is also running on an outdated version of Drupal:

A little further checking show that the Drupal version is 7.36, 7.37, or 7.38, which means they haven’t applied any updates since at least August of last year .