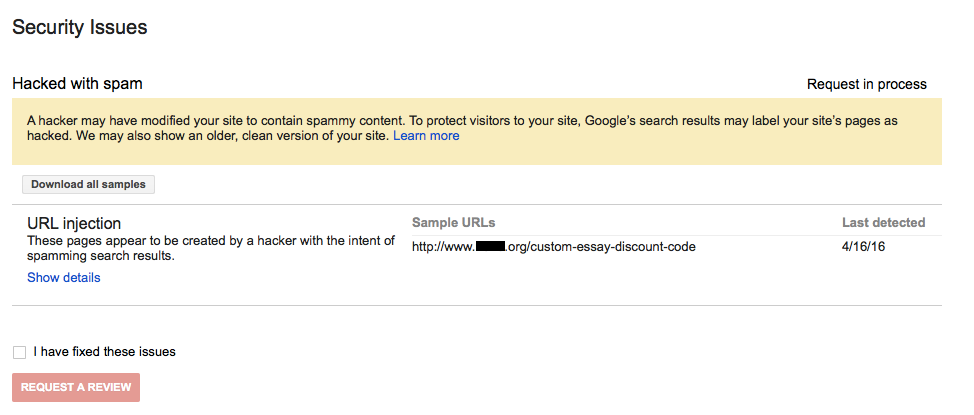
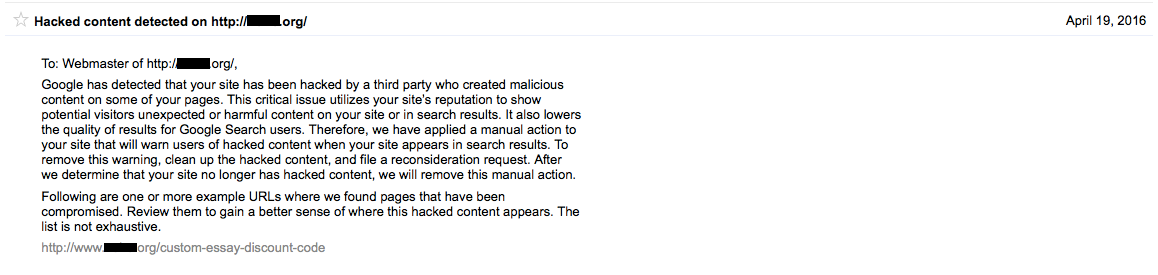
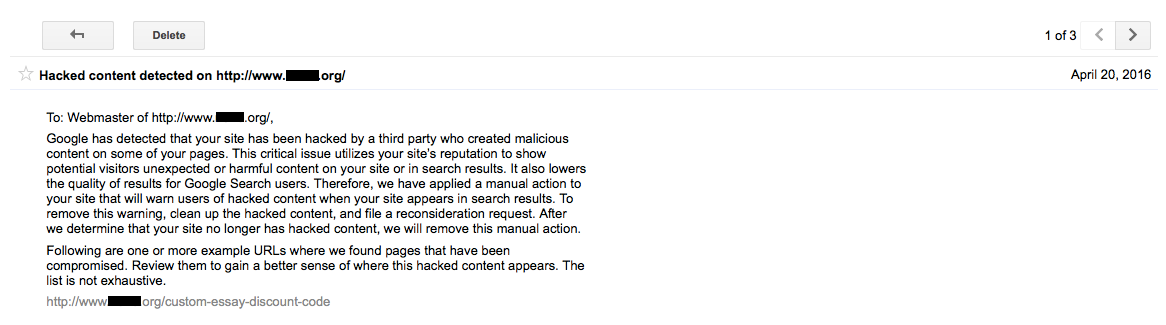
Over the past couple of years we have run across a lot of bad stuff involving the security company SiteLock, from not doing basic security checks to not doing basic parts of hack cleanups to breaking websites they are supposed to be cleaning to labeling a website that is very dangerous for visitors as being “secure”. Unfortunately those kinds of things are really par for the course when it comes to security companies (it is a really sleazy industry in general). But recently we have started to see and hear more that indicates that SiteLock has gone past that and moved to more egregiously cheating their customers. Making this more of a problem, is that they now have partnerships with many web hosts, which gives them additional legitimacy that they shouldn’t have considering the multitude of problems we have see involving them.
One of the issues that we see coming up a lot involves SiteLock charging a monthly fee to protect websites and then when the website gets hacked they want a much larger amount to clean up the website. If the website is getting hacked then the protection being paid for doesn’t seem to be actually happening or isn’t very good. There also seems to be an incentive for the protection they provide to not actually protect, since they can actually make even more money if it doesn’t work.
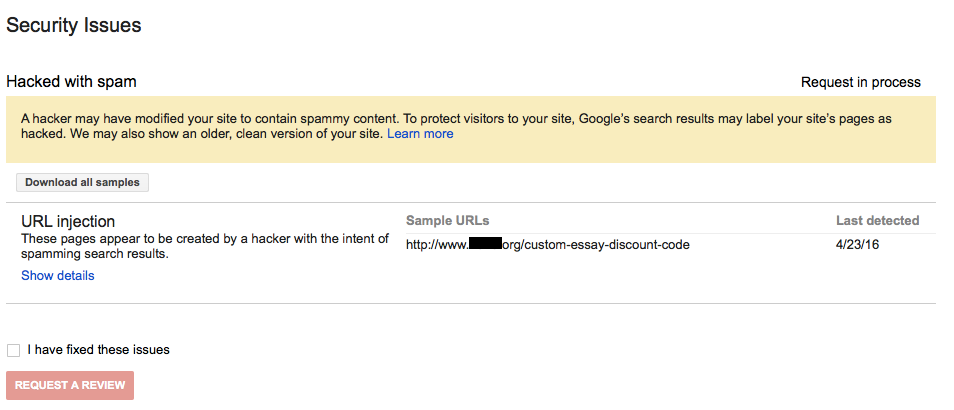
The other that comes up is fairly frequently is them contacting people claiming that a website has been hacked and that they can clean it, without SiteLock actually checking to see if the website is actually hacked. One example of that we were contacted about involved a website that had been actually hacked, for which the person who took over resolving that decided to start fresh, only reusing the domain name. So the website would have been clean at the point that SiteLock contacted them, which didn’t stop SiteLock from charging them for a cleanup:
When the site was hacked, the domain was blacklisted by every major blacklister, however,since I built the new site from scratch, it was clean when it went live. In spite of that, Sitelock contacted me the day after bringing the new site live that they were in the process of cleaning malware from the site and to contact them as it was going to involve manual removal and additional costs above what the plan that came with WordPress covers. They offered me two options, 300 to clean the site and submit to the blacklisters for review or 299 (in three installments) to clean the site and provide manual removal coverage for three months, after which I could continue with the scan and removal tool and add manual removal coverage for 49.00 per month from then on.
Beyond the fact that SiteLock was charging them for an unneeded cleanup, a website shouldn’t need continuing removals of malicious code. If that is the case, that would usually indicate that the original hack cleanup wasn’t done properly and the hacker could get back in, in that case the person who did the original hack cleanup should go back in and get the issue fixed for free (we certainly would want to do that for a client).
What SiteLock then did for that monthly fee doesn’t sound great either:
I have not been able to make it even a week (in two months) without Sitelock sending me some scary critical security warning email concerning the site. One of them said that they were cleaning malware, which I had a hard time believing since I had really good passwords, 2 step verification and login limiting onthe site. It turned out, the “malware” was a file that was created when I installed the Ithemes security plugin.All the other warnings were the result of them constantly not being able to connect and access the files in ordder to scan, which I don’t understand since I had not changed the passwords and each time, the problem ended up being resolved without a clear explanation as to how or why it happened in the first place.
Based on what we are seeing we have some recommendations if you are contacted by SiteLock or if your web hosts is recommending using them:
Get a Second Opinion
Based on what we are seeing it sounds like SiteLock sometimes is claiming that websites have been hacked that haven’t actually been hacked, so it would be a good idea to get a second opinion as to whether you have been hacked when you are contacted by them.
This is a good idea in other instances as well, since we sometimes see web hosts claiming a website has been hacked due to issues that were caused by something that was actually unrelated to a hack or them not double checking results of antivirus scanners (which can produce some bad false positives).
We are happy to do a free check to see if a website is actually hacked (we always will do that before taking on the clean up of a hacked website), so we are happy to provide you with a second opinion.
Hire Someone Who Properly Cleans Up Hacked Websites
If your website has in fact been hacked it is important to make sure you are hire someone that does a proper hack cleanup. You don’t want to be like many of our clients who hire to us to re-clean their hacked website after the first company they hired didn’t do those things.
The three main components of a proper hack cleanup are:
- Cleaning up the malicious code and other material added by the hacker.
- Securing the website (that often means getting the software on the website up to date).
- Attempting to determine how the website was hacked.
While determining how the website was hacked is often not possible to do due largely to web hosts failure to store log files on a long term basis (something that we found SiteLock had not rectified with at least one of their hosting partners), we have found going through the process is important to get a hacked website fully cleaned. If the source of hack hasn’t been determined then that increases the chances that the security issue hasn’t been resolved and that the website will get hacked again.
We would recommend asking the companies what there hack cleanup service involves and if they don’t mention that they do those things, then you probably should look elsewhere.
Securing Your Website
One really important thing to understand it isn’t naturally for websites to get hacked. For that to happen something must have gone wrong. So the solution to keeping your website secure is to make sure you are taking the proper security measures with your website, instead of going with a security product or service that doesn’t do those things and instead make bold claims that it will keep you secure some other way.
It also important to understand that the chances of a website being hacked are pretty small, so when you see people saying that they use a service and haven’t been hacked, it is entirely possible that the service had nothing to do with them not being hacked.