Recently we have discussed about how someone (or someones) at WordPress is disappearing some of our posts from the their support forum, including an instance where the original poster was left with only bad information from a forum moderator, while our post with the solution to their issue was deleted. Why they are doing that is a mystery, but the end result is that public is left without important information like in that case. While looking over the most recent round of this we noticed that whomever is doing this feels the need to hide what is going on from the public by deleting not just our posts, but in one case deleting a benign response from someone else thanking us, which would have made it obvious that our post was removed if that response remained.
Before we get into the details of the disappeared posts, it worth noting what is supposed to a reason to have a post deleted or edited from the forum:
Generally speaking, posts are only edited or removed where to do otherwise might lead to serious consequences. Previous examples have included posts that accidentally incorporated proprietary code or where the poster asking has reason to fear for their online safety. Having a posted site url come up in Google in NOT a serious consequence. In each case, use your best judgement or ask for a second opinion. If the final decision to to leave the post “as is”, use something like:
When a post is made and people contribute answers to an issue, that then becomes part of the community resource for others to benefit from. Deleting posts removes this added value. Forum topics will only be edited or deleted if they represent a valid legal, security, or safety concern.
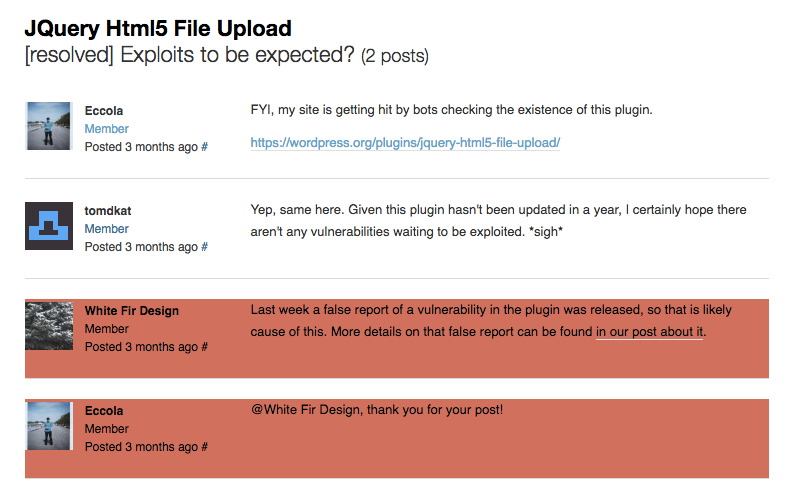
Back in April someone posted on the support forum for the JQuery Html5 File Upload plugin, indicating they were seeing bots checking for the existence of the plugin and wondering if their were exploits to be expected in the plugin. Shortly after they we responded, explaining that the likely cause of this was a false report of a vulnerability in the plugin that was released a week before. The original poster then responded thanking us for the information, “@White Fir Design, thank you for your post!”. Earlier this week as part of the latest purge our post was deleted, though as this screenshot of the changes made shows it wasn’t the only thing deleted (the posts with a red background were removed):
You can see that they not only removed our post, but the response to it. The response couldn’t possibly have lead to “serious consequences” if it remained and there is no “valid legal, security, or safety concern” that could have required it to be deleted. So the only explanation left is that whomever deleted our post wanted to cover up the fact that they were doing that from the public, since if the reply remained it would be obvious that another post by has had been removed.
Among the other posts deleted was another reply about a false report of a vulnerability:
What would be a “valid legal, security, or safety concern” that would require that to be deleted?
In another thread a post was removed were we provided a timeline of a hacking campaign and suggested someone to review the log files for their website to determine the source of the hacking:
Again, what would be a “valid legal, security, or safety concern” that would require that to be deleted?
The final situation we will highlight is a little different, in this case they didn’t delete a whole post, instead they just deleted a sentence mentioning that the people running the Plugin Directory have failed to notice that vulnerabilities still existed in plugins and linked to a page that discussed the problem:
It is quite troubling that someone is trying to sweep under the rug a serious and ongoing problem with WordPress’ handling of security issues in plugins, instead of working on making sure that the problem doesn’t happen anymore.