When it comes to the security of websites what we see is that basic security measures are often not being taken with websites, while security companies push additional security measures without evidence that they provide better protection than doing the basics or in addition to doing the basics. Considering how bad the security industry is, it probably isn’t surprising to hear that we have repeatedly found that security companies themselves are not doing the basics, while pushing additional security measures.
Back in October we looked at one cyber security company that claimed to have “clients in the intelligence community, DoD and nearly every cabinet agency” that wasn’t keeping the WordPress and Drupal installations on their websites up to date, while telling people that they doing the additional security step of vulnerability scanning isn’t enough and that they need penetration testing done as well (which not surprisingly they offer). From what we have seen it looks like a lot of penetration testing largely involves running automated tools that try exploit known vulnerabilities in software, which usually would not exist if you are keeping your software up to date.
In November we looked at a couple of other cyber security companies that had been in news that were also running outdated software on their websites.
Today let’s look at example of this from the WordPress security world, which shouldn’t be all that surprising if you follow our blog. In the past we have mentioned the security company Wordfence in regards to their scary lack of security knowledge and pushing the falsehood of of brute force attacks against WordPress admin logins (which they are still pushing).
Over at the blog for our Plugin Vulnerabilities service today we looked another instance where Wordfence’s very popular security plugin failed to prevent exploitation of a plugin vulnerability (the 14 other security plugins we tested also failed to prevent exploitation), this vulnerability is one that you can’t protect yourself against by keeping your plugins up to date, so it would be something where an additional security measure could actually be useful (the companion plugin for our service has been warning webmasters of that vulnerability since Monday).
While working on that we ran across the Wordfence Official Documentation portion of Wordfence’s website and noticed they are running an outdated and insecure version of MediaWiki on that:
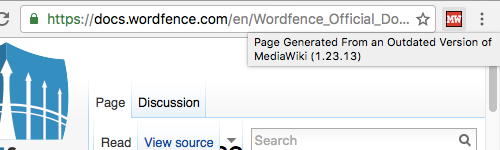
Both versions 1.23.14, release in May, and 1.23.15, released in August, contain a number of security fixes.