When it comes to the security of WordPress websites one of the impediments to improving it is that security industry likes to make up threats and then claim they will protect against them, which makes it harder to get people to focus on things that would actually improve security of their websites.
One example of this that was fairly popular for a while was to claim that WordPress listing what version of WordPress was in use in the HTML code of the website was a security risk and that they had a solution. It didn’t really make any sense for a number of reasons.
First, if the developers of software were really doing something that intentionally puts you at risk, the solution seems like it should be to use different software not try to undo them putting you at risk.
Second, hackers usually wouldn’t bother checking if a website was running WordPress, much less what version was in use, before trying to exploit a vulnerability. So if you were using an outdated version of WordPress with a vulnerability that could be exploited (we haven’t have seen a vulnerability in WordPress be the cause of a large scale hacking for maybe a decade at this point), no matter how hard you tried to hide the version it wouldn’t impact whether the vulnerability would get exploited. The real way to prevent the exploitation would be to keep WordPress up to date.
Third, if a hacker wanted to know what version of WordPress was in use, then hiding the listing of version number wasn’t actual effective at the time as they could simply check for changes in JavaScript or CSS files to determine the version in use. That wasn’t a secret, but either the people promoting this either never bothered to a search to see it had been pointed out or they ignored it.
A Strong Password Is The Real Solution
The latest example of this type of thing involves a new feature introduced in WordPress 4.7, which was release earlier this month. The REST API added in this version provides “machine-readable external access to your WordPress site with a clear, standards-driven interface”.
Cue that being claimed to be a security issue, in particular the user portion of it, which the plugin Wordfence Security, used on 1+ million websites according to wordpress.org, started blocking access to shortly after. In a discussion on that the WordPress.org Tech Guy, who we have had a bit of interaction in dealing with WordPress on vulnerabilities in WordPress plugins, he responded to it this way:
Why do people still think this a real issue? Your Twitter username is exposed to everybody. Is that a real problem?
What really happened here is that WordFence added code to break the API. Simple as that. Usernames are not private information, in any sane system. Use good passwords. Then it doesn’t make any difference what your username is.
My username on my site is “otto”. Best of luck to ya.
That all sounds reasonable and he expanded on that in a follow-up response.
Here is part of the response from Wordfence:
Security is all we do. The WordPress.org core team and contributors have a different focus and a different world-view. Many of our team spend all day fixing hacked WordPress sites and working directly with traumatized customers who are incredibly stressed because their business has stalled and their data has been stolen.
We don’t arbitrarily implement features. Our design decisions are based on thousands of hours of human experience working with hacked sites, looking at attack data and understanding the wide variety of our customer’s needs.
While they claim they don’t “arbitrarily implement features” and “decisions are based on thousands of hours of human experience working with hacked sites”, no where in their response do they even make a claim that the feature would likely lead to websites being hacked. There is a good reason for that, it wouldn’t.
In the post announcing the feature they do give a reason for doing it, but it is even worse than none:
This can be exploited by bots that are launching brute-force password guessing attacks on WordPress websites. They can use this API to list the usernames of anyone who has published a post on a WordPress site. The list of users displayed via this API almost always includes a user with admin level access.
Despite Wordfence repeatedly pushing the idea that brute force attacks against WordPress admin passwords are happening (and that their plugin is the solution), they simply are not happening. At best Wordfence doesn’t understand what is actually going, which are dictionary attacks, not brute force attacks. Those involve a hacker trying to log in using common password and there is a really simple way to protect against them, use a strong password. It doesn’t matter if someone has your username, those attacks will fail as long as you use a strong password. If Wordfence told the truth about what is happening it would also remove a reason to use their plugin, which might also explain why they keeping pushing that falsehood.
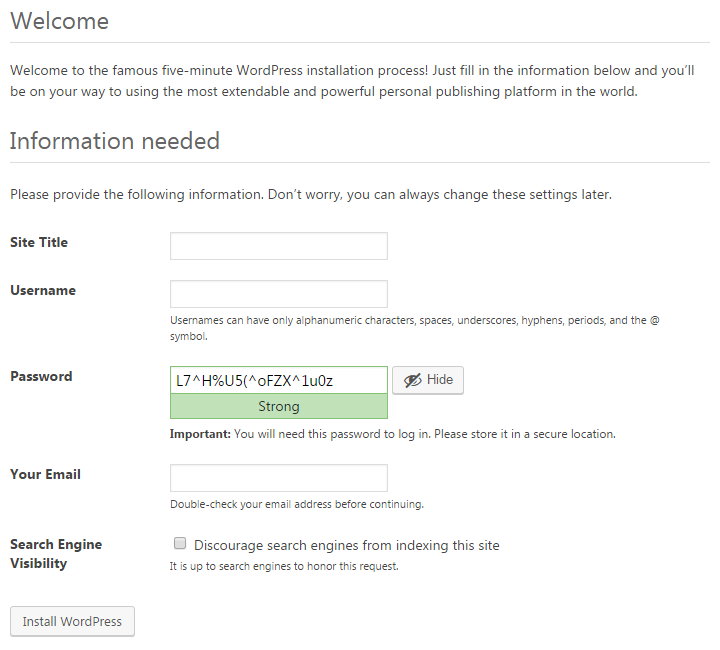
WordPress does a good job on helping people to use a strong password. When setting up WordPress it will pre-populate a strong password for you:
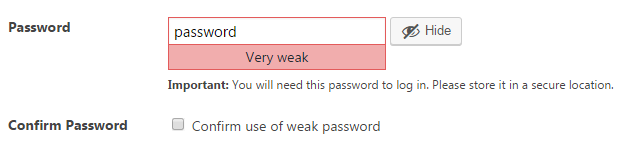
Let’s say you decide to use a weak password instead. Not only will the password strength indicator tell you it is “Very weak”, but you will need to check a box to “Confirm use of weak password”:
About the only other thing they could do in terms of make sure a strong password is used is making its usage mandatory, which has some downsides.
Wordfence Lack of Concern For a Real Source of Hacked Websites
Going back to Wordfence’s explanation for creating an issue where there isn’t one, it read in part:
Security is all we do. The WordPress.org core team and contributors have a different focus and a different world-view. Many of our team spend all day fixing hacked WordPress sites and working directly with traumatized customers who are incredibly stressed because their business has stalled and their data has been stolen.
At the same time it turns out they are actually okay with people using their plugin being hacked. Before we get to that let’s look at how their plugin is described on the Plugin Directory:
Secure your website with Wordfence. Powered by the constantly updated Threat Defense Feed, our Web Application Firewall stops you from getting hacked.
and
Wordfence Security is 100% free and open source. We also offer a Premium API key that gives you Premium Support, Country Blocking, Scheduled Scans, Password Auditing and we even check if your website IP address is being used to Spamvertize.
So it is free and will stop you from being hacked right? Well not always.
On November 20 the security company NinTechNet, makers of the security plugin NinjaFirewall, were cleaning up a hacked website and discovered that the source of the hacking was a arbitrary file upload vulnerability in the plugin Delete All Comments, which recently had 30,000+ active installs according to wordpress.org. They contacted the developer and didn’t receive a response, they later notified the Plugin Directory and it was removed. On December 10, they disclosed the issue publicly.
On December 11 it was added to a public database of WordPress vulnerabilities, the WPScan Vulnerability Database. On December 12 it was added to the free data that comes with the companion plugin for our Plugin Vulnerabilities service.
Also on December 12 we saw the first interest in the plugin by hackers with the data we monitor for Plugin Vulnerabilities service, which probably also indicates that widespread exploitation would have begun then as well.
On December 16 we did a test to see if security plugin could prevent exploitation of these over at our Plugin Vulnerabilities service. Seeing as the vulnerability had not been fixed (and still hasn’t), so keeping your plugins up to date would not protect you, this is situation where a security plugin could provide some. Unfortunately none of the 15 plugins we tested prevented the vulnerability from being exploited.
One of the plugins tested was Wordfence, so here is a situation where websites are being hacked, the plugin didn’t stop it from happening and you have people that are going to be, to use Wordfence phrasing, “traumatized customers who are incredibly stressed because their business has stalled and their data has been stolen”.
Only on December 16 did Wordfence take any action on this:
We developed a firewall rule for that exploit and released it into production on December 16th, the moment we heard about it from our users.
And only because their users notified them. And it turns out that was only because of us:
In the case of the vulnerability above, we heard about it because you were making some noise about it. Our users alerted us.
That is quite a poor response, when you consider that simply monitoring one of two publicly available sources of information of vulnerabilities could have lead to a response days sooner, instead of relying on their users to do it for their work for them. But at least people using the plugin are safe now, right? Wrong.
Instead only websites using their paid service will get protected for a month:
The rule is now in production for Wordfence Premium. It will only be available in the free Threat Defense Feed 30 days after release, so around Jan 15th.
So everyone else will be open to being hacked for a month, with a vulnerability that Wordfence knows is already being exploited, since that was how it was discovered.
While leaving people using their plugin vulnerable to be exploited is bad for them, it could actually pay off for Wordfence since they also do hack cleanups.
Even the people with the paid service are getting poor service, as Wordfence wasn’t proactive in protecting them, instead relying on users to let them know of the issue, after the exploitation looks to have taken off. What is particularly striking about that is they market their paid service very differently. In promoting the Real-Time Threat Defense Feed that is part of that, they say:
Wordfence protects over 1 million WordPress websites, giving us unmatched access to information about how hackers compromise sites
The unmatched access could actually be outmatched by simply monitoring public sources. It isn’t just this vulnerability, through our Plugin Vulnerabilities service we repeatedly found apparent zero-day vulnerabilities, which are vulnerabilities being exploited before the developer is aware of them, in WordPress plugins and every indication is that Wordfence was not aware of them (that also makes you wonder about their claim that they have “thousands of hours of human experience working with hacked sites, looking at attack data”). In some cases it looks like hackers were exploiting those vulnerabilities for more than a year before we had started monitoring the data that helped us to identify them and take further action.
Wordfence Should Stop Misleading The Public
If Wordfence wants to leave people relying on their plugin vulnerable like they have with the vulnerability in Delete All Comments, they have a right to do that, but they should be honest with people about what is going on and not say things like that they put the community first, when the actually put profits before them.
It would also be good if they stop making up threats as well.